Configuration of the CI/CD environment.
Make sure to place the configuration (config.json) file which was created during the setup of the project with the desktop app see here, in the root of the repository under .safe folder. For more information about the config.json file please visit here.
Example of a configuration file that is output from the setup wizard.
{
"output": "stdio",
"version": "1.0",
"project": {
"type": "erlang",
"name": "erlang_project",
"appbases": [
"_build/default/lib"
],
"excludes": [
"/test/"
],
"includes": [
"apps/services/include",
"apps/custom_cmd/include",
"apps/config/include",
"apps/alarms/include"
],
"extra_paths": [
"apps/plugin/priv"
]
}
}
Define the CI/CD Job
In your CI/CD pipeline, define a job specifically for the security audit tool (e.g., security-check). This job will manage the analysis process by referencing the configuration created in the desktop application.
Warning
If the Erlang code generates additional modules then please include a dedicated job or step in the CI pipeline to handle code generation. This should run before the SAFE test. SAFE needs to have access to all the erlang files that are part of the application.
Here is an example definition for github actions, CircleCI and SemaphoreCI.
Github actions
name: Erlang CI
on:
push:
branches: [ "main" ]
pull_request:
branches: [ "main" ]
permissions:
contents: read
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- uses: erlef/setup-beam@v1
with:
otp-version: '24'
hexpm-mirrors: |
https://builds.hex.pm
https://cdn.jsdelivr.net/hex
rebar3-version: '3.20.0'
- name: Compile
run: rebar3 compile
- name: Upload _build directory
uses: actions/upload-artifact@v3
with:
name: build-artifact
path: _build
security-check:
runs-on: ubuntu-latest
needs: build
container:
image: erlangsolutions/safe:1.0.1-otp-24
steps:
- name: Download _build directory
uses: actions/download-artifact@v3
with:
name: build-artifact
path: _build
- uses: actions/checkout@v4
- run: safe start
env:
SAFE_LICENSE: ${{ secrets.SAFE_LICENSE }}
- name: Persist results
uses: actions/upload-artifact@v3
with:
name: project-safe-results
path: _results/<<Project_Name>>.safe
CircleCI
security-check:
resource_class: medium
docker:
- image: erlangsolutions/safe:1.0.1-otp-24
working_directory: /repo
steps:
- checkout
- attach_workspace:
at: /repo
- run:
command: safe start
no_output_timeout: 1h
- store_artifacts:
path: /repo/_results/<<Project_Name>>.safe
SemaphoreCI
version: v1.0
name: Erlang
agent:
machine:
type: e2-standard-2
os_image: ubuntu2004
blocks:
- name: build
task:
jobs:
- name: compile
commands:
- rebar3 compile
env_vars:
- name: MIX_ENV
value: test
dependencies: []
- name: Security Check
dependencies: []
task:
jobs:
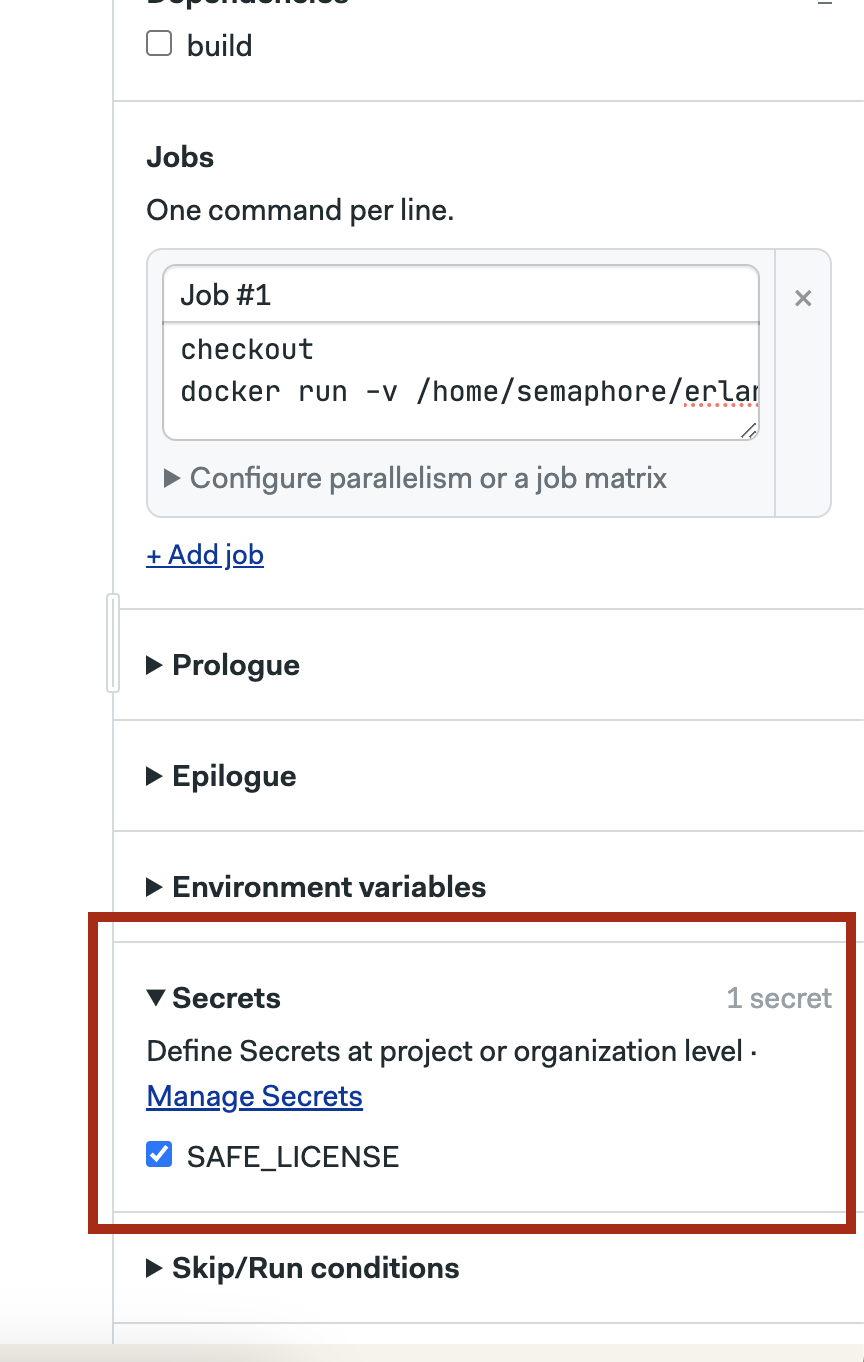
- name: 'Job #1'
commands:
- checkout
- 'docker run -v $(pwd)/_results:/safe/_results -v /home/semaphore/<<Repository>>:/repo --env SAFE_LICENSE="$SAFE_LICENSE" erlangsolutions/safe:1.0.1-otp-24'
- artifact push job _results/<<Project_Name>>.safe
secrets:
- name: SAFE_LICENSE
Tip
If you're unsure about the name of your project, simply review the first few lines of the SAFE job output. SAFE will display the project name there to guide you.
To create and use secrets in SemaphoreCI please visit the documentation.
Info
The minimum system requirements for the CI machine are 2 CPUs and 4GB of RAM.
Example result in the ci output:
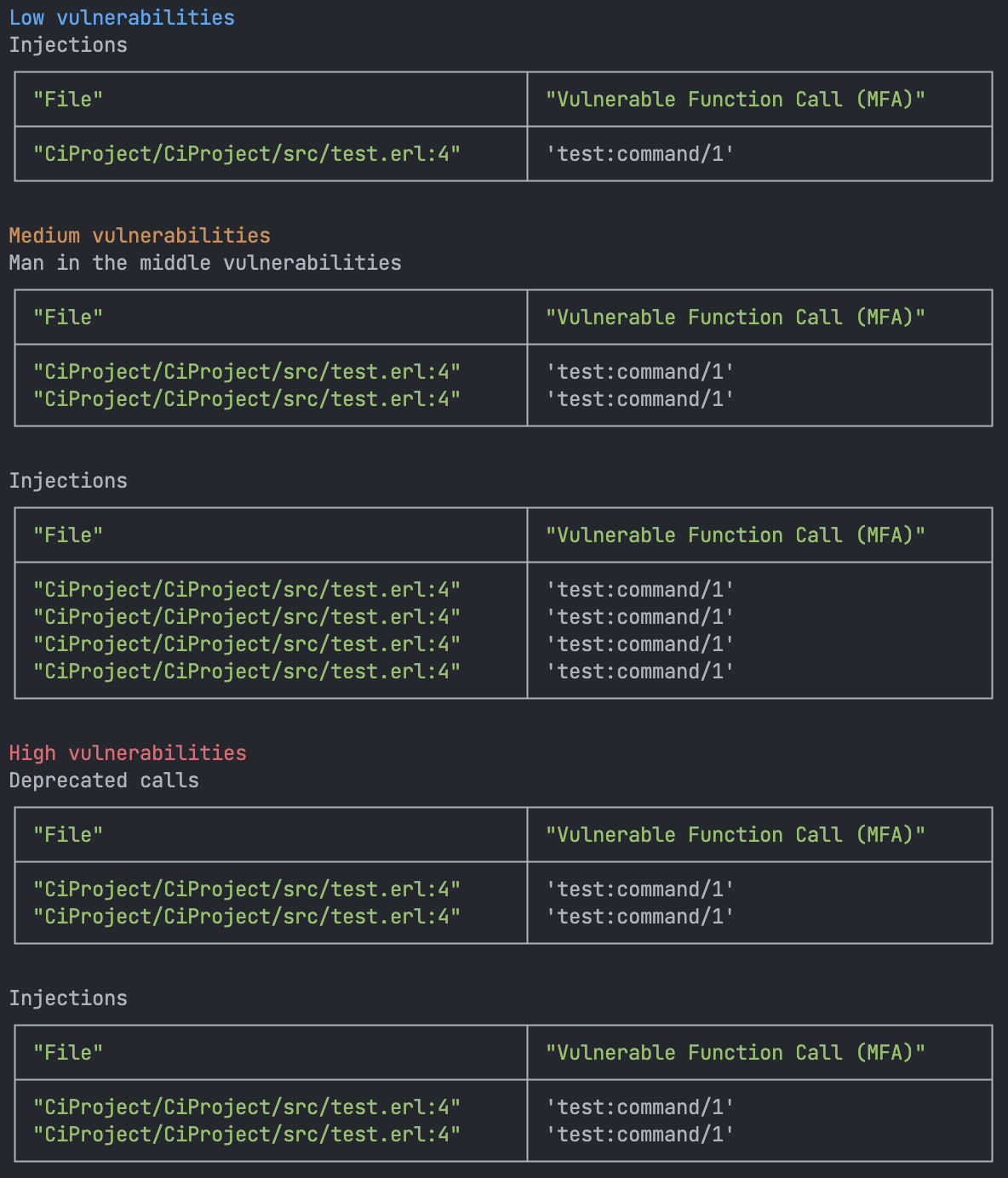
the CI job will terminate with exit code 1 in case SAFE finds vulnerabilities