Reports
Info
To explore the report of the vulnerabilities, please import the resulting file of the CI/CD run into the Desktop application, more information here.
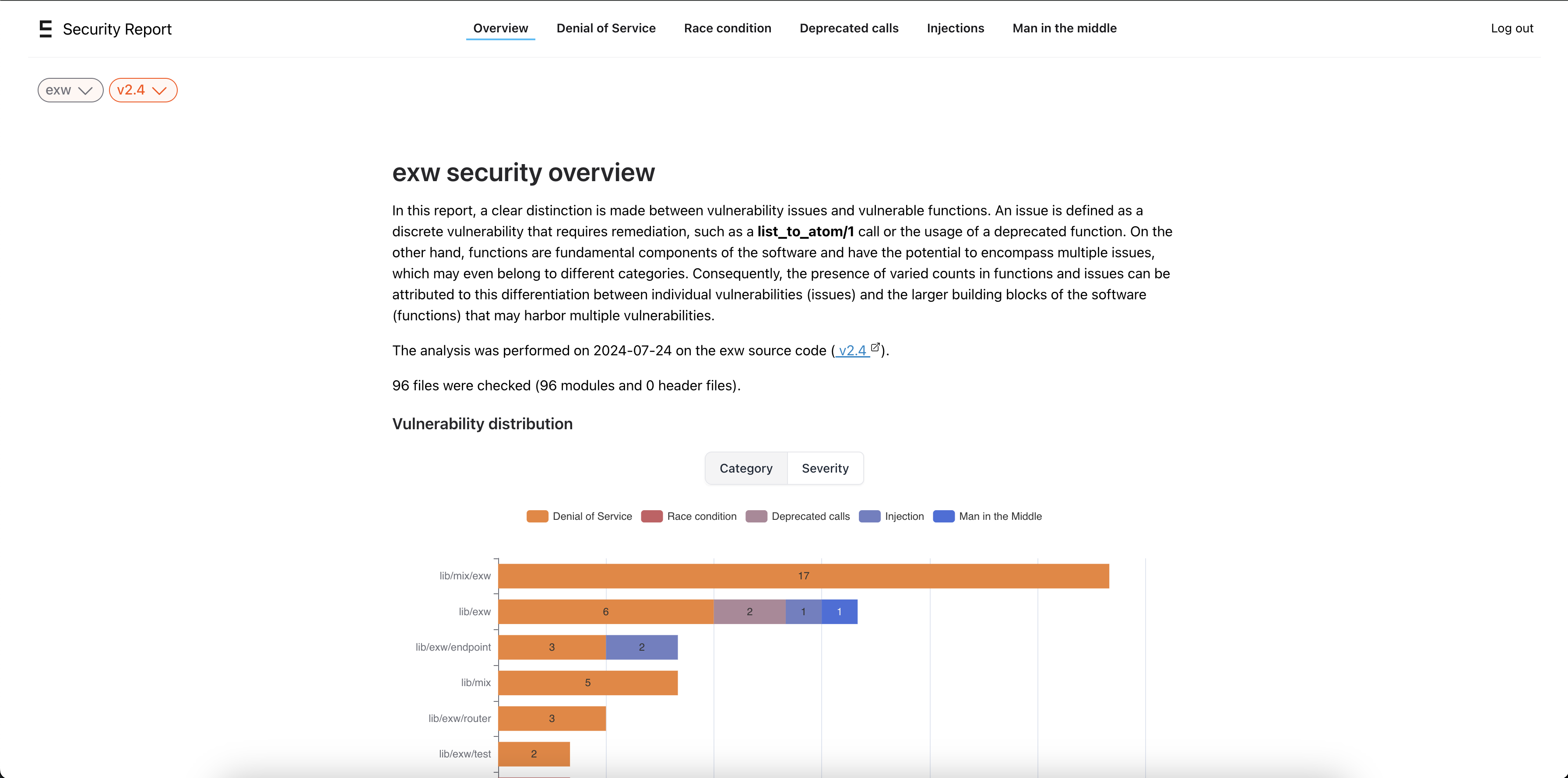
The security overview gives a summary of the vulnerabilities found in the software. The overview aims to help team leads and managers to easily identify the major security weaknesses in the code base.
To visualize the report please add the resulting file from the CI artifacts results.safe
Denial of Service
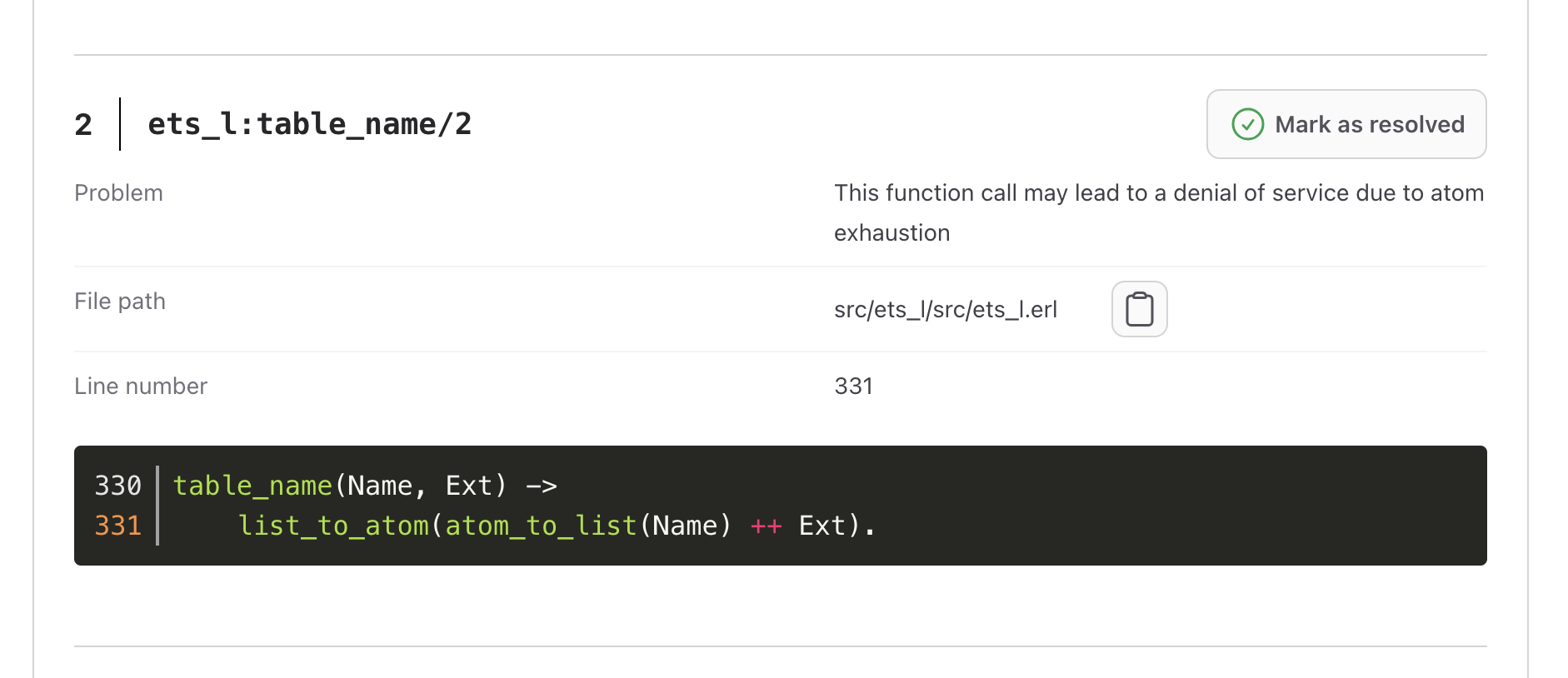 In Erlang, we manage unique atom values through a global atom table. As your system runs, new
atom values are automatically added to this table as needed. It’s like expanding a dictionary with
new words.
However, here’s the technical bit: we don’t remove entries from this table once they’re in there.
The table’s size is initially set based on system configuration, usually around a million entries.
If you ever attempt to add a new value when the table is already full, it can cause the virtual
machine to crash. So, it’s important to configure this table size wisely to ensure the smooth
operation of your Erlang system.
In Erlang, we manage unique atom values through a global atom table. As your system runs, new
atom values are automatically added to this table as needed. It’s like expanding a dictionary with
new words.
However, here’s the technical bit: we don’t remove entries from this table once they’re in there.
The table’s size is initially set based on system configuration, usually around a million entries.
If you ever attempt to add a new value when the table is already full, it can cause the virtual
machine to crash. So, it’s important to configure this table size wisely to ensure the smooth
operation of your Erlang system.
Race condition
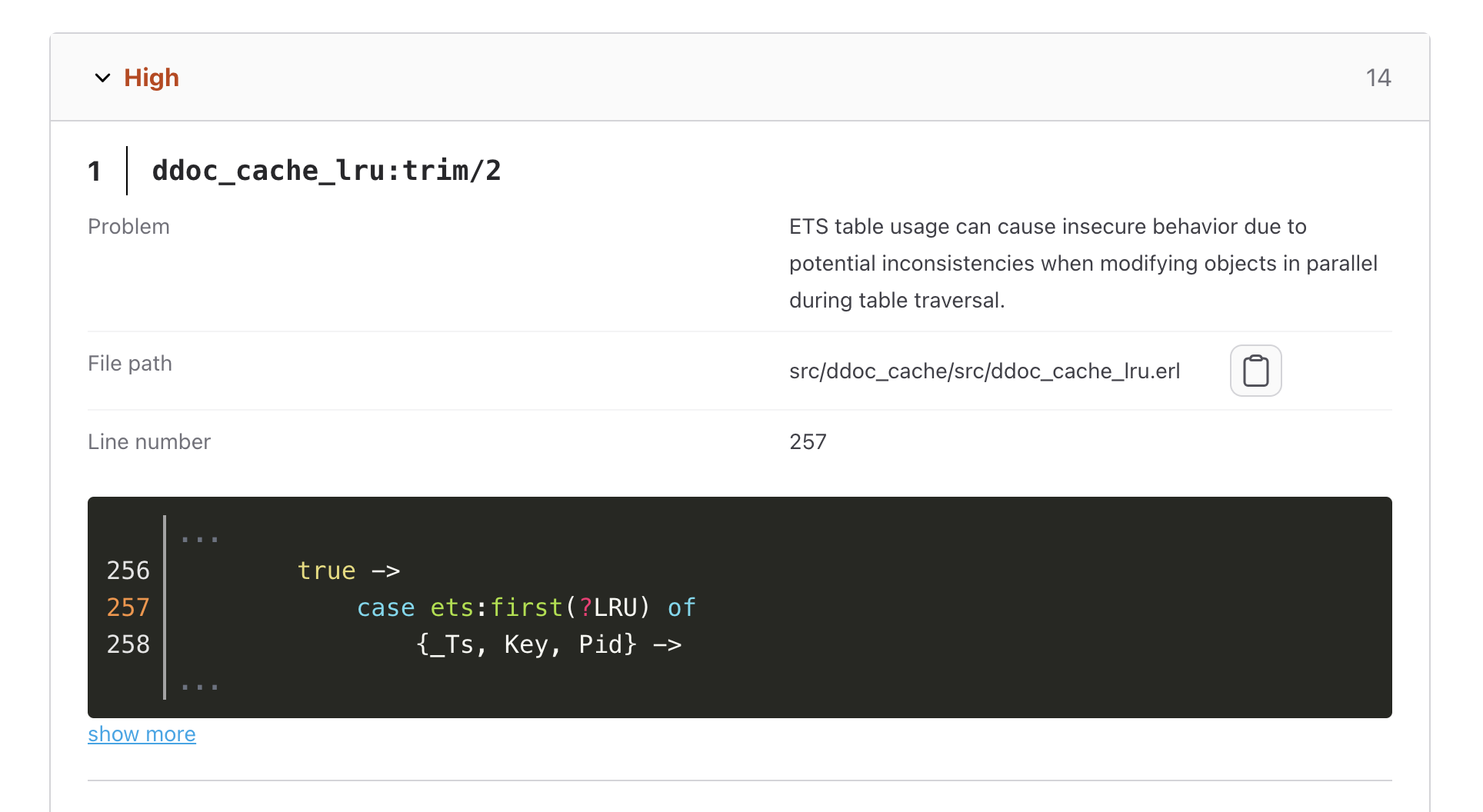
Erlang is not entirely immune to race conditions, despite its concurrency model. Race conditions can occur in databases like Mnesia, where simultaneous access by multiple processes to shared resources may lead to unpredictable results. In Mnesia, for instance, race conditions may arise when processes attempt to read or write data concurrently, potentially resulting in data inconsistencies, lost updates, or unexpected application behavior. Although Erlang’s design helps mitigate these risks, careful synchronization and transaction handling in databases are essential to ensure data integrity and consistent system behavior.
Deprecated calls
As with many programming languages, Erlang periodically needs to deprecate certain functions to enhance security and improve the ecosystem's overall robustness. Some of these deprecations are prompted by identified security vulnerabilities, such as those in the crypto module, which pose a risk to applications if left unaddressed. Failure to update or replace deprecated functions can expose systems to potential attacks, undermine data integrity, and lead to non-compliance with industry security standards. By proactively monitoring these changes, businesses can mitigate security risks, ensure system reliability, and maintain secure, stable, and compliant operations across their applications.
- Deprecations: Link
Injections
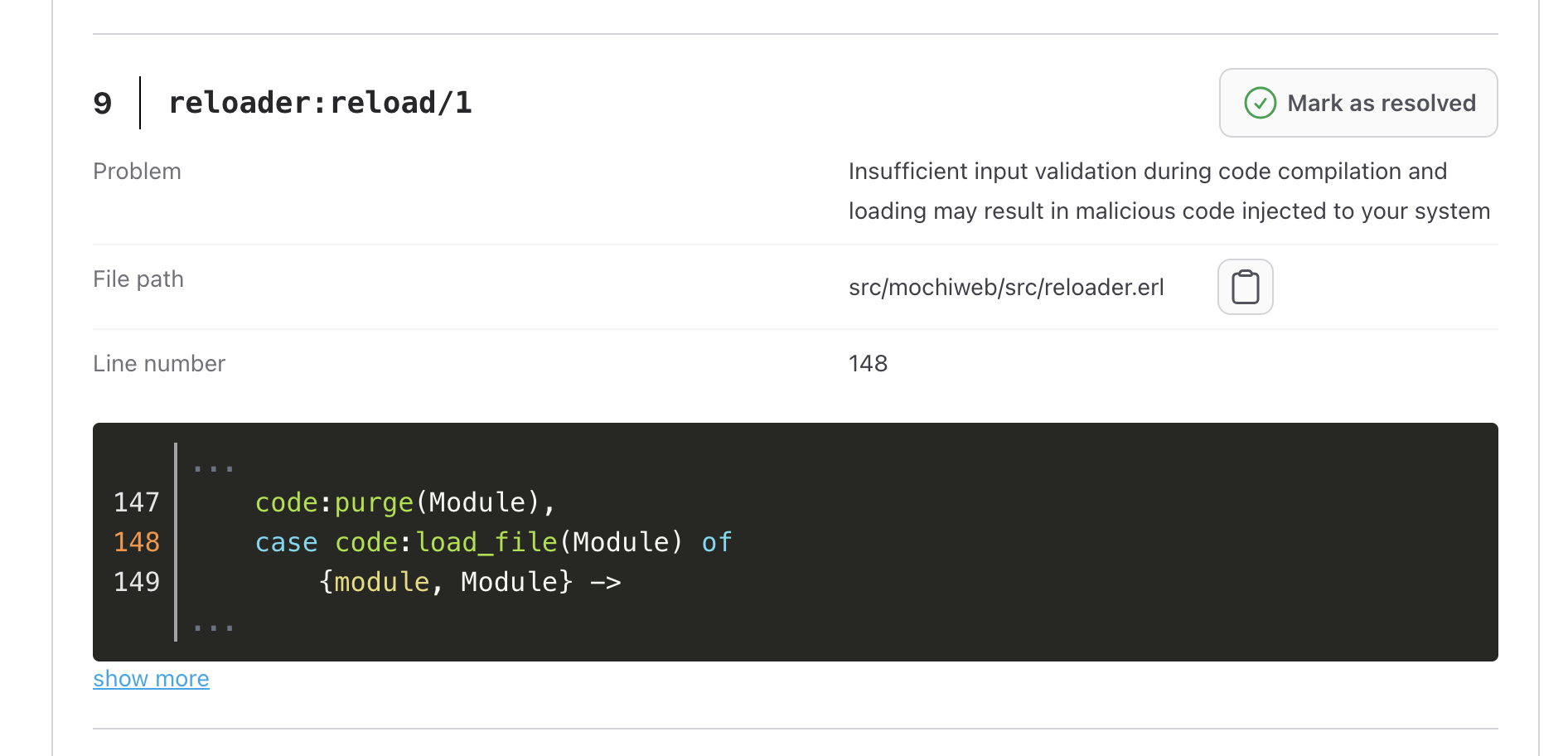 Erlang is renowned for its ability to dynamically upgrade code in real-time, allowing new versions of modules to be loaded and executed without interrupting system operations. However, this feature can also introduce security vulnerabilities, as it opens the door for incompatible, erroneous, or even malicious code to be introduced into the system. Without rigorous validation, untrusted or flawed updates could lead to significant risks, including data leaks, system instability, or crashes. To safeguard against these threats, it is essential to implement strict controls and monitoring around dynamic code upgrades, ensuring that only verified, secure code modifications are applied to the system.
Erlang is renowned for its ability to dynamically upgrade code in real-time, allowing new versions of modules to be loaded and executed without interrupting system operations. However, this feature can also introduce security vulnerabilities, as it opens the door for incompatible, erroneous, or even malicious code to be introduced into the system. Without rigorous validation, untrusted or flawed updates could lead to significant risks, including data leaks, system instability, or crashes. To safeguard against these threats, it is essential to implement strict controls and monitoring around dynamic code upgrades, ensuring that only verified, secure code modifications are applied to the system.
Man in the middle
A man-in-the-middle (MITM) attack is a critical security threat that occurs when a cyber attacker intercepts and reroutes a communication channel, positioning themselves between two parties to capture, view, or even alter the data exchanged. In the context of Erlang’s crypto library, the risk of MITM attacks becomes especially concerning if deprecated or vulnerable cryptographic functions are still in use. Attackers could exploit outdated encryption methods, compromising the integrity and confidentiality of communications. As Erlang deprecates certain crypto functions for stronger alternatives, it is vital to adopt these updates to mitigate vulnerabilities